So one of the most common things that I come across when talking to businesses of all sizes is that they spend a large amount of time and effort to protect their employees laptops and desktops but seem to have forgotten about the “Mobile Computers” that the majority of users are carrying around.
I always seem to hear the same line of “Its ok we have MDM that provides the security for our mobiles”. Yes the clue is in the name Mobile Device Management, not Mobile Device Security!!
When considering the right products for your organisation there are some key questions to ask with regards to Mobile Devices (Smart Mobile (Cell) Phones and Tablets).
Question 1: What access does the Mobile Device have to my organisations data?
Every organisation is different and some users will only use a mobile device for Multi Factor Authentication (MFA) via the likes of Microsoft Authenticator or Google Authenticator. However most organisations will allow mobile devices to access email, chat, file sharing services and many more. It is key for an organisation to identify what access these devices have to then be able to apply risk based controls to limit the subsequent exposure should a device become lost or compromised.
Question 2: Is this an organisation owned device or is it a Bring Your Own Device (BYOD)?
So this is a key consideration for nearly all organisations. Due to the pandemic there were a lot of organisations that had to switch from completely on premise (office bound) systems to having all their staff working from home literally overnight. This in turn meant that for some personal devices (BYOD) were allowed to then access organisations data to ensure the business could continue successfully. This brought with it a large risk as the age and security of these devices are an “Unknown” and as such could cause an organisation a greater level of risk.
Question 3: Do you have your own organisational Application Store or can users install any application?
If an organisation is managing their mobile devices via an MDM solution then there should be an approved application store where administrators have pre-approved applications that users can download and install. These MDM solutions do also allow genuine applications from the likes of the Apple Store or Google Play Store. The organisation just needs to be aware that these apps are not always 100% secure and there are continual apps being removed as being malicious from both stores. If the organisation allows BYOD then this compounds the risk as users have full control over their devices.
Question 4: Are you already managing your organisational mobile devices by an MDM solution?
There are many different MDM solutions on the market with Intone and Knox being just a couple. These MDM solutions allow you to manage the devices (once onboarded)and control the applications and policies that are applied. BYOD devices may not be able to be onboarded using this method even though the tools support the break between Personal and Corporate ownership. It will be down to the employee (user) to decide if they are happy to have their device managed.
So now we have identified the key questions it is time to look at putting a security wrap around the data that these mobile devices have access too. This is where Mobile Endpoint Security products come to save the day.
There are a number of MES products on the market:
- Better Mobile
- BlackBerry Protect Mobile
- Check Point Harmony Mobile
- Lookout for Work
- Microsoft Defender for Endpoint
- MVISION Mobile
- Pradeo
- Sophos Mobile
- Symantec Endpoint Protection Mobile
- Wandera Mobile Threat Defense
- Zimperium
Taking a closer look at one of the products: Lookout for Work
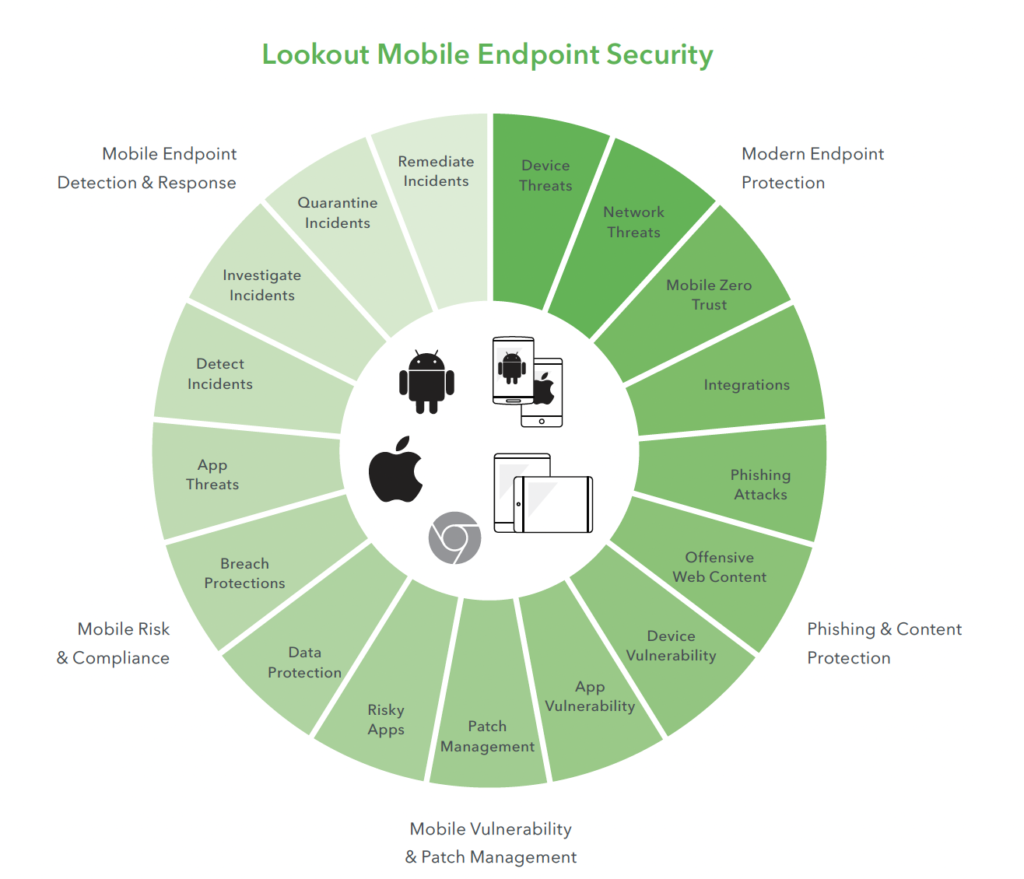
Lookout Mobile Endpoint Security
Advanced cloud-delivered mobile security to protect any device that goes everywhere you do
The move to remote working has seen more and more organisations rely on mobiles and tablets to routinely access corporate data. However, a big problem amongst corporate businesses is that mobile security is often overlooked, which can create a gap in security architecture.
While the cyber threats on mobile devices are similar to desktops, securing them requires a completely different approach. Since the use of mobile devices goes hand in hand with the Cloud, an endpoint-to-cloud security solution makes the most sense to add to your architecture. Lookout Mobile Endpoint Security is an endpoint-to-cloud solution designed to address the ever-evolving mobile security requirements.
Delivered via the cloud, Lookout protects iOS, Android, and Chrome OS with endpoint detection and response built by expert threat researchers. Being cloud-based, it removes friction, increases usability and convenience, enables user freedom and reduces operational costs when compared to a collection of standalone solutions.
Powered by the Lookout Security Graph, it scales to hundreds of thousands of endpoints, uses an optimised lightweight app for processor performance and battery life, and cloud modules enable you to customise the solution to meet your needs.
For more information please visit: https://www.lookout.com/products/mobile-endpoint-security
